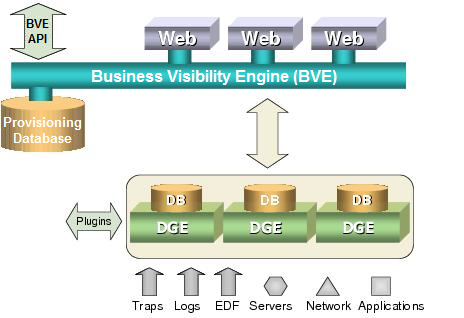
Traverse uses a three-tier architecture consisting of the Business Visibility Engine (BVE), the Provisioning Database, and one or more Data Gathering Engines (DGEs). All configuration and authentication information is stored in the Provisioning Database.
For enterprises, all of the Traverse hardware can exist at one central location or be geographically distributed to accommodate multiple offices or divisions. One DGE can monitor all the devices at a single location, including servers, routers, switches, applications, and network appliances. The DGE measures and stores aggregated performance data locally, and forwards only events or alarms to other Traverse components. For a data center environment, Kaseya recommends that you employ a DGE at each data center location and set up the provisioning and authentication database at a central location (for example, your NOC).
Traverse System Overview
The Traverse system comprises three main components. In a large environment, Kaseya recommends that each component reside on its own host server.
Although these architectural components are designed to reside on different servers, Traverse allows you to configure two or more components on a single server.
DGEs schedule and perform tests, archive and aggregate data, and trigger notifications and actions. Effective management of historical information is done by setting bounds on storage that prevent it from growing to unmanageable limits. Historical records are aggregated and stored for over a year by default. Historical alarm and event data (changes in severity level) are retained without aggregation and only aged by user selection.
During the initial installation, you can import existing department or device records, or a subset thereof, into the Traverse Provisioning Database using the BVE API. The system comes with default thresholds for all tests, which you can automatically update using the baselining feature after operating Traverse for a few days.
If you are using firewalls within the data center, you must configure access through the firewalls to enable the monitoring of the devices behind them. If the number of devices behind a firewall is significant, you can connect the DGE to a port behind the firewall. Also, if you are using Network Address Translation (NAT) or private address space, the IP address must be unique within the data center.