The Logon Policy page sets logon policies that apply to all VSA users. Logon policies prevent a brute force break-in to the system. By limiting the successive number of bad logon attempts and disabling rogue accounts for a set amount of time, you can prevent unauthorized access achieved by repeatedly entering random passwords.
Note: See VSA Logon Policies for a summary of functions affecting user logons.
Specify the bad logon attempt policy
Note: To activate the account manually before the lockout time elapses, another user must enable the account using the System > Users page.
Note: The inactivity timeout applies to the VSA web interface and Live Connect application. It does not apply to Remote Control sessions.
Note: If left blank, the domain checkbox still does not show on the logon page until at least one domain logon exists. Domain logons can be added using Discovery > Domain Watch.
Specify password strength policy
IT Complete Single Sign-On Integration
VSA servers with release 9.5.11b (build 9.5.11.4396) or later have the option to integrate the VSA login process with IT Complete (Kaseya One) Single Sign-on, without requiring any VSA license update. In 9.5.16b (build 9.5.16.5619) the authentication and registration workflow was simplified. Follow these steps to register the VSA at organization level with a Kaseya One company account, and then associate individual VSA user accounts to their respective Kaseya One users.
Workflow Overview
Note: Their KaseyaOne user account must belong to the same company that their VSA organization is mapped to.
To map their own VSA organization to a KaseyaOne company, a Master or a System role VSA administrator must complete these steps:
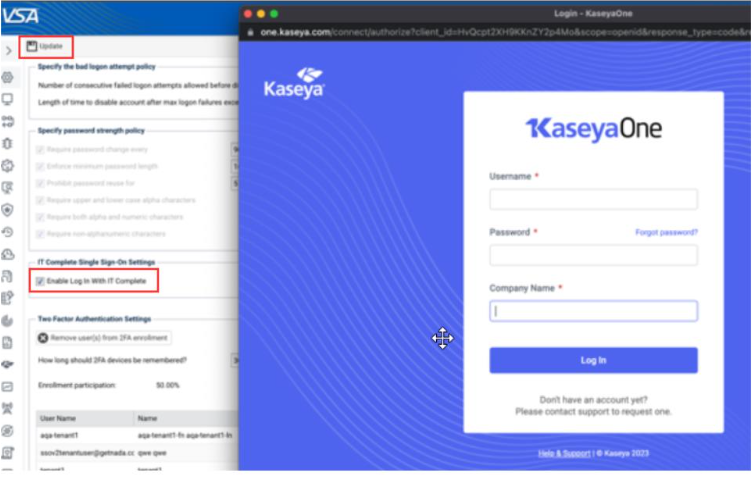
To map another VSA organization a KaseyaOne company, a Master or System role VSA administrator must complete the following steps.
Note: Multiple VSA organizations can be mapped to the same or different KaseyaOne companies. If the same VSA administrator needs to map organizations to different KaseyaOne companies, they will need to provide different KaseyaOne credentials each time. In order to avoid credentials from a current login session being used, they should log out of KaseyaOne prior to performing this step.
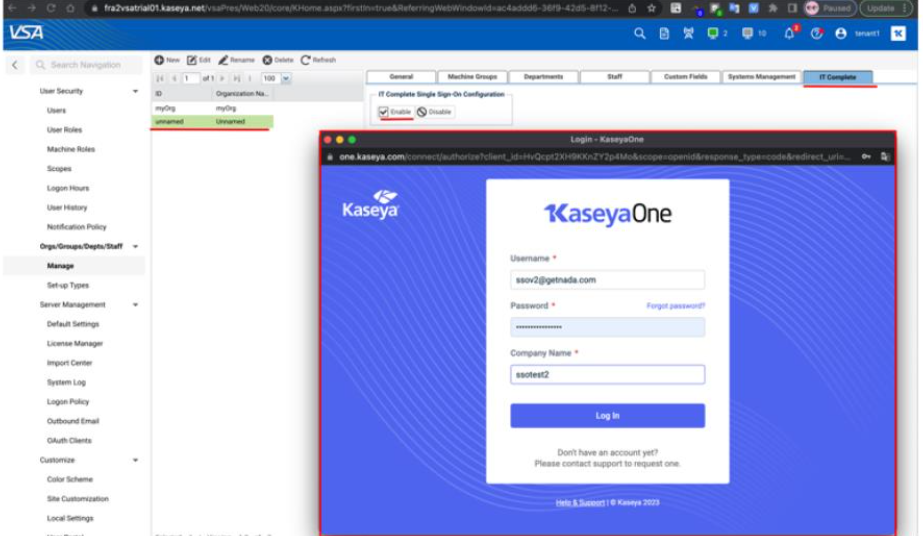
To register VSA user accounts with Kaseya One accounts each user within the mapped organization(s) can use the VSA login page or their user menu to enable Login with IT Complete.
To register VSA user accounts with KaseyaOne accounts for the VSA Login page.
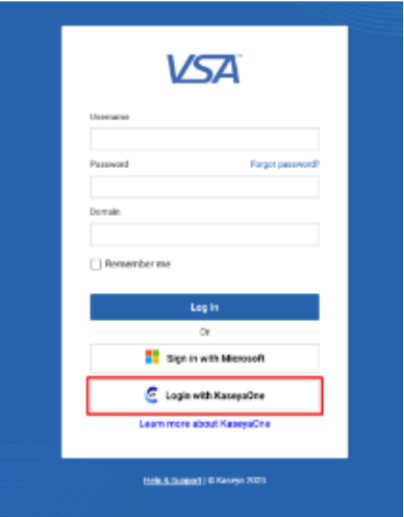
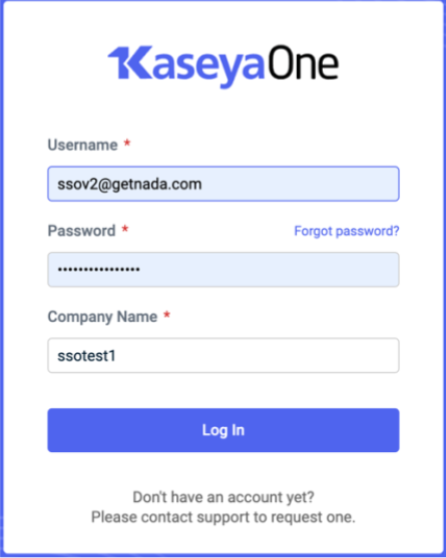
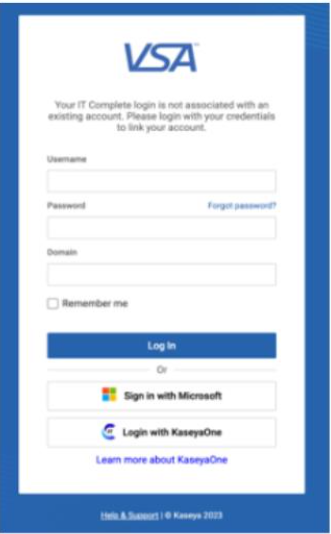
Now your VSA account is registered with your KaseyaOne account. You can log in to VSA using your KaseyaOne credentials
To register VSA user accounts with KaseyaOne accounts from the UserMenu :
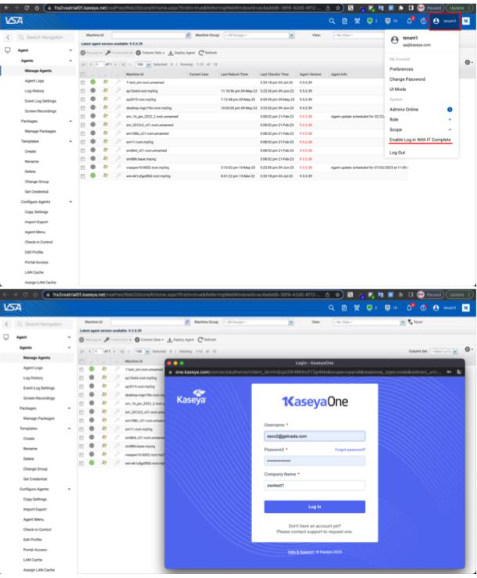
Now your VSA account is associated with your KaseyaOne account. You can now log in to your VSA using your KaseyaOne credentials.
To remove the association of your VSA account and KaseyaOne account:
Now your VSA account and IT Complete are disassociated.
Two Factor Authentication Settings
By default, 2FA is set to optional for all VSA tenants. To add security to user accounts within a tenant, it is recommended that each tenant configures 2FA as a mandatory login process.
To enforce 2FA in VSA for all user within a tenant:
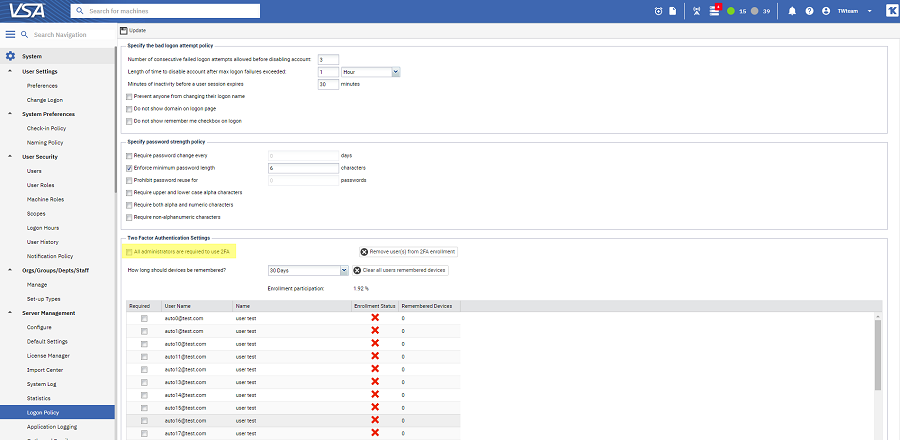
Now every user within the tenant will have to follow the 2FA process to login their VSA account.
To enforce 2FA in VSA for particular user(s) within a tenant:
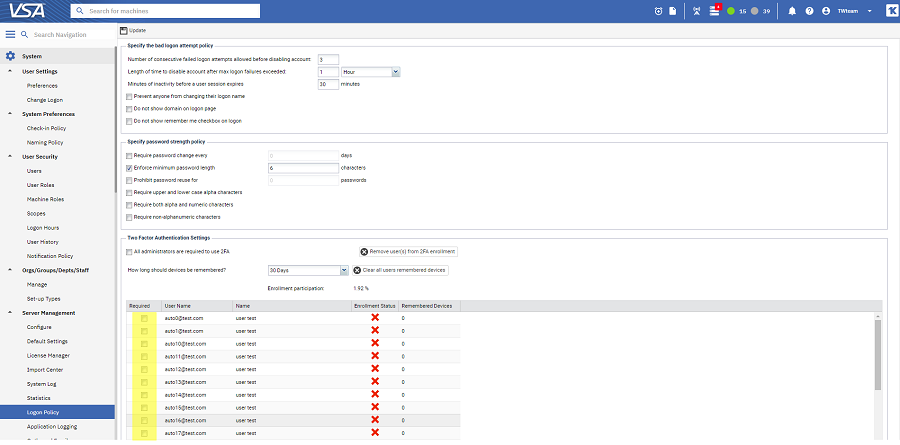
Note: If you do not have the checkboxes to select particular users, please make sure you have the All administrators are required to use 2FA checkbox unselected.
Now the selected user within the tenant will have to follow the 2FA process to login their VSA account.
2-Factor Authentication Enrollment Process Monitoring
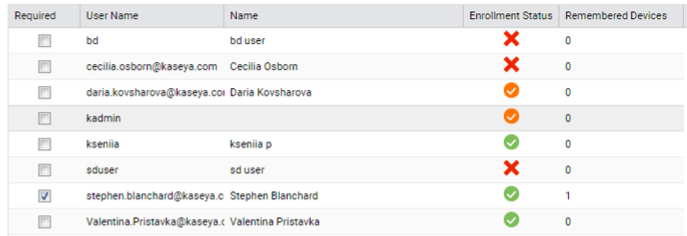
VSA Users with the corresponding permissions can monitor the status of 2FA enrollment process by Enrollment Status per each user within a tenant.
Currently, there are three 2FA Enrollment Status available:
![]() - user is not enrolled in VSA 2FA.
- user is not enrolled in VSA 2FA.
![]() - user is successfully enrolled in VSA 2FA.
- user is successfully enrolled in VSA 2FA.
![]() - user is partially enrolled in VSA 2FA. It means that user has not completed the 2FA enrollment process by entering the TOTP for some reason. These users will have to complete the 2FA enrollment process upon next log in.
- user is partially enrolled in VSA 2FA. It means that user has not completed the 2FA enrollment process by entering the TOTP for some reason. These users will have to complete the 2FA enrollment process upon next log in.
To monitor 2FA Enrollment Status of each user:
2FA Rest Options
VSA Users with the corresponding permissions can reset the 2FA enrollment status for each user within a tenant in any 2FA Enrollment phase. This is helpful, for example, if users have completed the 2FA enrollment process, but for some reason they cannot log into VSA successfully.
There are 2 ways for a Master or System Role User to modify a user's 2FA enrollment:
Note: Removing user's devices will not unenroll the User from 2FA. The user will have to enter a one-time password.
To remove 2FA Remembered Devices for all users
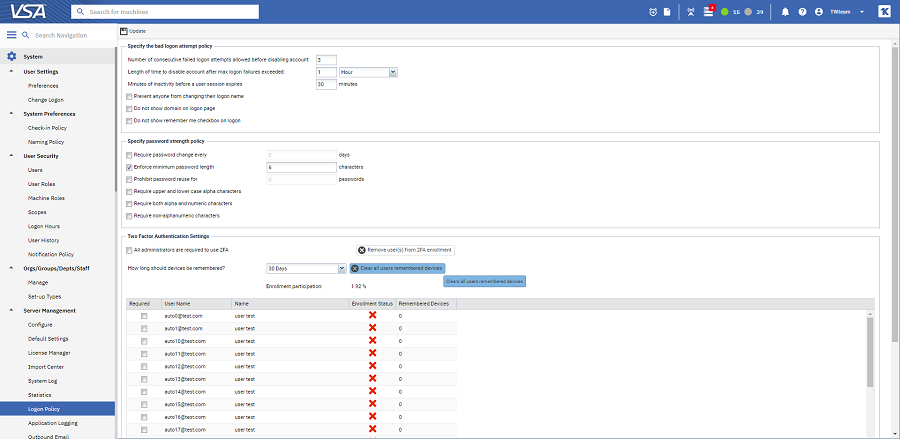
Note: The 2FA Enrollment Status for all users within a tenant will stay unchanged after clicking the Clear all users remembered devices button.
To unenroll a particular user or multiple users
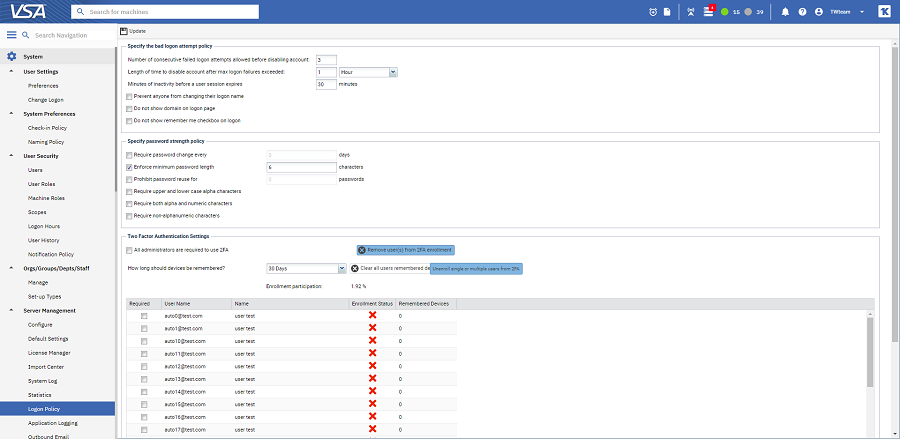
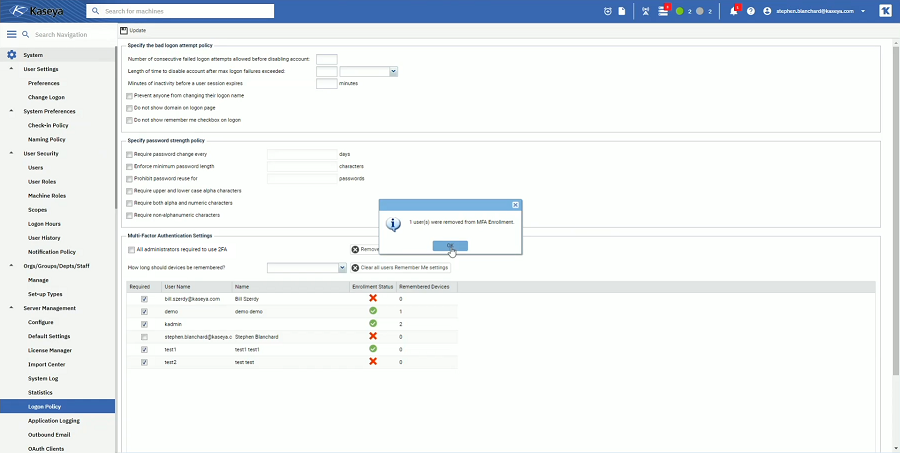
Note: Users removed from the 2FA Enrollment will have to complete the 2FA enrollment process next time they log into the VSA.
Note: See Two-Factor Authentication topic to set up authenticator application.
Update
Press Update to apply the settings.