The Network tab:
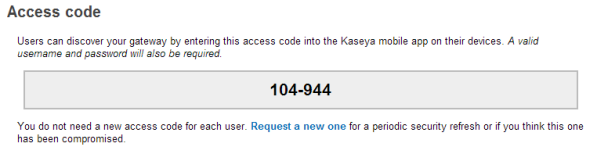
Access Codes
A BYOD Suite mobile device users must enter an access code—a six-digit number—to identify the BYOD gateway they want to access. The gateway administrator must include that access code when creating an invitation for mobile device users to logon to a BYOD gateway. You do not need a new access code for each user. Each user logon also requires a valid username and password.
Relay vs. Direct
There are two checkboxes on the Network tab that determine two different ways for clients to communicate with a gateway.
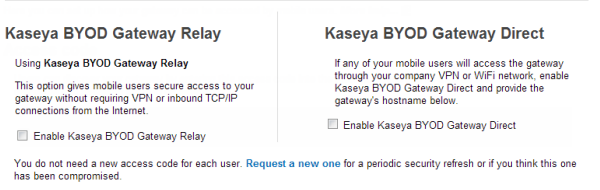
Kaseya BYOD Gateway Relay
If this option is checked, mobile device users are given secure access to your gateway without requiring VPN or inbound TCP/IP connections from the internet. Using this object requires not further configuration on the gateway administrator's part. Relay is a separate cloud service maintained by BYOD Suite.
Relay allows secure exchanges between mobiles and gateways behind a firewall. Information is fully encrypted in transit and at rest on the devices for best-in-class protection of your data. The mobile devices never become network nodes, increasing security and reducing the need to manage devices.
If your gateway reports any errors using this method, verify your firewall is not blocking outbound connections to the relay service. See Verify Relay Service for more information.
Port 443 is the outbound port used by a gateway to communicate with the relay service over SSL. There is no inbound port used by the relay connection.
Kaseya BYOD Gateway Direct
If this option is checked, mobile device users are required to make use of a company's own VPN or WiFi network to connect to the company's BYOD gateway. This option can improve performance for mobiles that are already on the corporate LAN through local WiFi connections or VPN tunnels. This option also enables corporations to deploy load-balanced clusters of gateways in DMZ's for high-volume situations, or where a DMZ deployment is preferred.
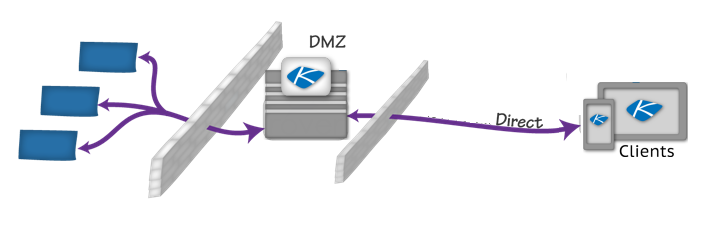
If this option is checked, you are prompted to enter your gateway's hostname and a port on which devices will connect to the gateway.
http://<selected hostname>:<selected port>/check into a web browser on a device that is on your local network. If the direct connection is setup correctly you will receive the following message: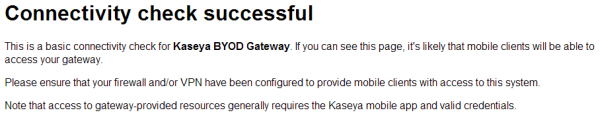
SSL Support
SSL support (https access) can be enabled for direct access. Using SSL requires a certificate and a private key, neither of which can be generated by the gateway. They must be provided by the gateway administrator. The key file must not contain a passphrase so it can run unattended.
By default SSL will be enabled if the gateway finds files called byodgateway-ssl.cer and byodgateway-ssl.key in the gateway's data directory. If different filenames or locations are needed, add these lines to byodgateway.ini:
portal_ssl_certificate = <full path to portal cert>
portal_ssl_private_key = <full path to portal private key>
Some SSL certificates require one or more intermediate certificates as part of an SSL certificate chain. The BYOD gateway requires a single SSL certificate file that contains the web server SSL certificate concatenated with all intermediate certificates creating a certificate bundle. This will produce a single certificate file with the intermediate certificates included at the end of the web server certificate. If you have a certificate that includes a certificate chain, check with your certificate provider to request a single file containing the certificate bundle.